-
Cyber-Security Framework: Recover
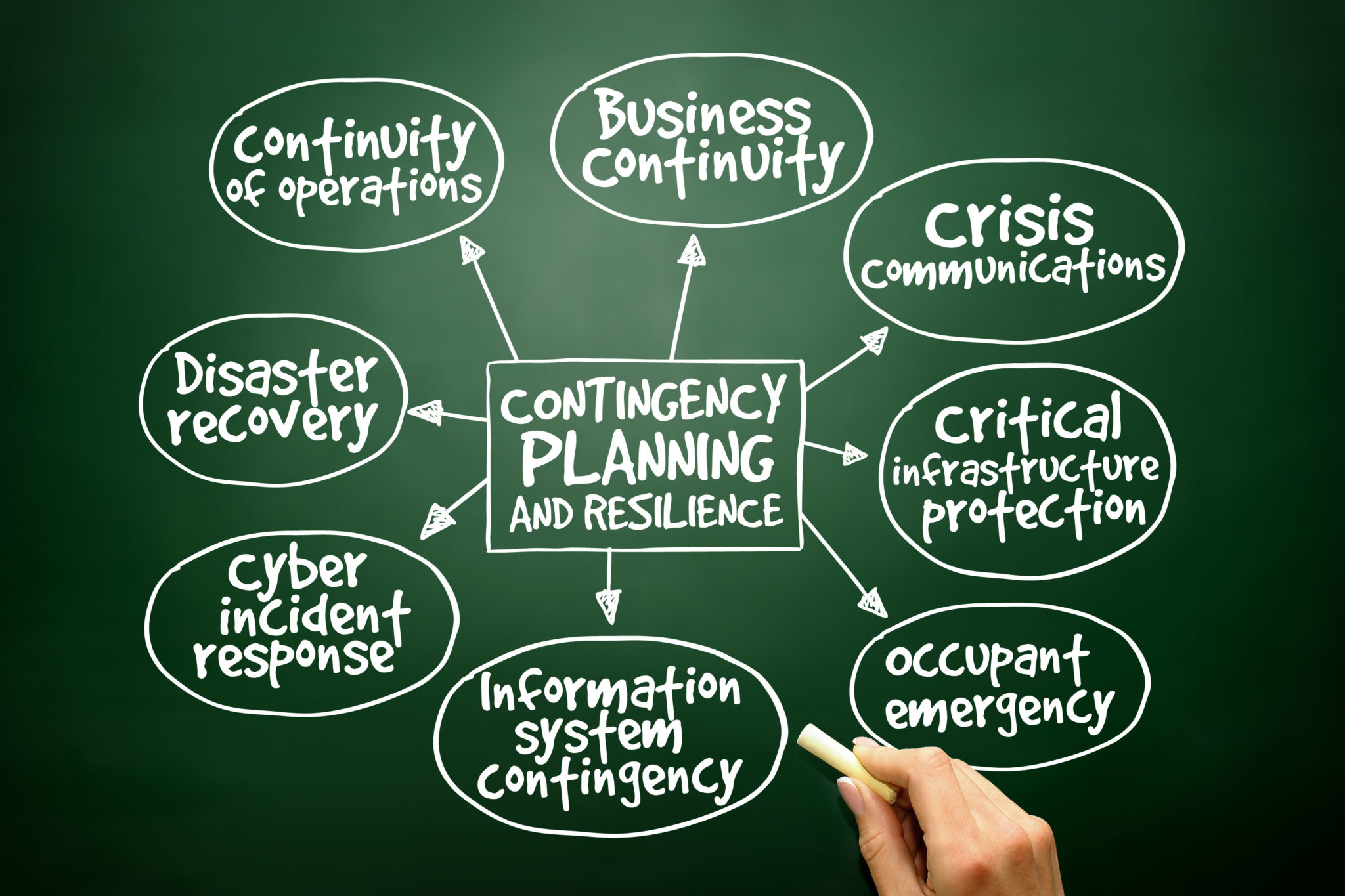
A written plan for processing critical applications in the event of a major hardware or software failure or destruction of facilities. What? The Recover Function identifies appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident. The Recover Function supports timely recovery to…
-
Cyber-Security Framework: Protect

The Protect Function supports the ability to limit or contain the impact of a potential cybersecurity event. What? Appropriate safeguards in place to ensure delivery of critical infrastructure services. How? Protections for Identity Management and Access Control within the organization including physical and remote access Empowering staff within the organization through Awareness and Training including…
-
Cyber-Security Framework: Detect

Identify the occurrence of a Cyber Security event to provide organization’s the ability to resolve in a timely manner. What? The Detect Function is to develop and implement the appropriate activities to identify the occurrence of a Cyber Security event. Similar to having items like smoke detectors and alarms installed in your home. These devices…
-
Cyber-Security Framework: Respond

Develop and implement appropriate safeguards to ensure delivery of critical services. What? Incident response is a well-planned approach to addressing and managing reaction after a cyber attack or network security breach. The goal is to minimize damage, reduce disaster recovery time, and mitigate breach-related expenses. How? Identify Management and Access Control Cyber-Security Awareness and Training Data…
-
Cyber-Security Framework: Identify

Provide the business insight into the Cyber-Security Risks in the organization so it can manage the cyber-security risk present in systems, assets, data, and Networks. Identify Asset Vendor Identify Asset Operating System Identify Asset Vulnerabilities Identify External and Internal Cyber-Security Risks Provide Actionable Data so Identified Risks can be Mitigated Develop Remediation Plan How? Conduct Level 1…
-
End Point Protection and Monitoring

Cyber threats to your organization are constant. An attack may slow your systems down, corrupt your data, or worse, bring your operation to a standstill. Chattertel can provide you powerful endpoint defense solutions that protects your business from harm.
-
Network Security

Network security tools require constant care, time, energy, and attention. Chattertel can provide day-to-day operation to keep your network security defenses in top performance. This way, your team can focus on the things that matter most.
-
Security Operation Center Team

Providing Continuous Security Our team of Cyber Security Experts acts as an extension of your internal IT team by expanding the capacity to monitor, detect, respond, and assist with mitigating Cyber Security Threats.